For an extended period, malevolent actors have utilized typosquatting as a strategy to deceive gullible individuals into accessing harmful websites or downloading software and packages containing hidden malware.
Typically, these assaults entail the registration of domains or packages with names that are somewhat different from those of their authentic counterparts (goog1e.com vs. google.com, for example).
Adversaries targeting open-source repositories across platforms have relied on developers making typing errors to initiate software supply chain attacks through PyPI, npm, Maven Central, NuGet, RubyGems, and Crate.
The latest findings from cloud security firm Orca show that even GitHub Actions, a continuous integration and continuous delivery (CI/CD) platform, is not immune from the threat.
“If developers make a typo in their GitHub Action that matches a typosquatter’s action, applications could be made to run malicious code without the developer even realizing,” security researcher Ofir Yakobi said in a report shared with The Hacker News.
Anyone can publish a GitHub Action by making a GitHub account with a temporary email address, which makes the attack possible. Because actions take place in the context of the user’s repository, it is possible for a malicious action to manipulate the source code, obtain confidential information, and use it to spread malware.
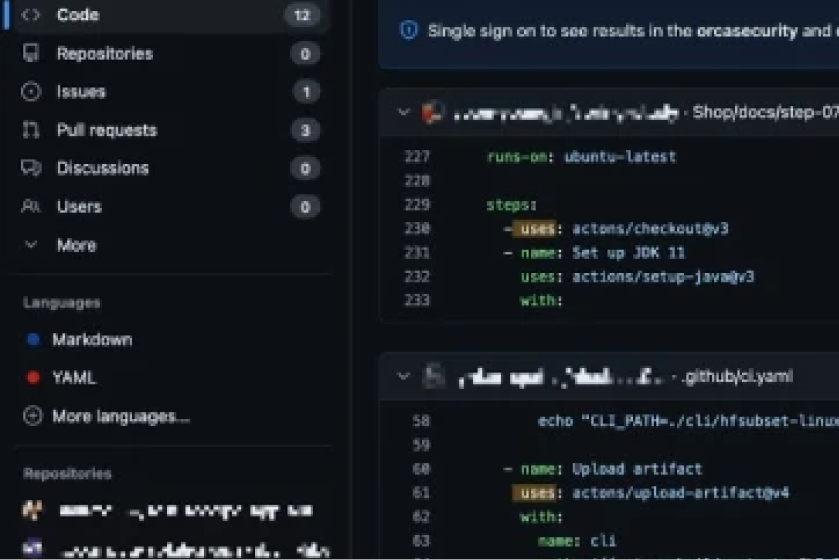
The attacker only has to create repositories and organizations with names that roughly mimic well-known or frequently used GitHub Actions in order to execute this approach.
The user’s workflow will execute the malicious action rather than the intended one if they accidentally misspell a GitHub action when setting it up for their project and the adversary has already produced the misspelled version.
“Imagine an action that exfiltrates sensitive information or modifies code to introduce subtle bugs or backdoors, potentially affecting all future builds and deployments,” Yakobi stated.
“In fact, a compromised action can even leverage your GitHub credentials to push malicious changes to other repositories within your organization, amplifying the damage across multiple projects.”
Orca said that a search on GitHub revealed as many as 198 files that invoke “action/checkout” or “actons/checkout” instead of “actions/checkout” (note the missing “s” and “i”), putting all those projects at risk.
Threat actors are drawn to this type of typosquatting because it is a low-cost, high-effect attack that has the potential to corrupt a software supply chain and disrupt multiple downstream consumers at once.
It is recommended that users verify that their names and actions are referencing the correct GitHub organization, only use actions that come from reliable sources, and routinely check their CI/CD workflows for typosquatting problems.
“This experiment highlights how easy it is for attackers to exploit typosquatting in GitHub Actions and the importance of vigilance and best practices in preventing such attacks,” Yakobi stated.
We are just spotlighting the aspects of the issue that are visible in public repositories here, which makes the real issue even more worrying. It is unknown how these errors may affect private repositories, where they may cause significant security breaches.”
0 Comments
No comments yet. Be the first to comment!













Post a comment