The vulnerabilities were found by cybersecurity investigators in Kia vehicles, which if not patched, could have allowed an intruder to operate critical vehicle functions through just its license plate details.
“Such attacks could be performed on a loaded vehicle within roughly 30 seconds irrespective of the fact that there is no active Kia Connect subscription, on any hardware loaded vehicle,” said the security experts Neiko Rivera, Sam Curry, Justine Rhinehart and Ian Carroll.
Most of the vulnerabilities almost impacted Every Kia produced out of 2013, and such vulnerabilities placed attackers in a position to quietly probe sensitive data such as the contact details of the vehicle owner.
The researchers suggested that such loopholes can be utilized to stealthily include the hacker as a secondary user of the vehicle, who cannot be seen by its real owner.
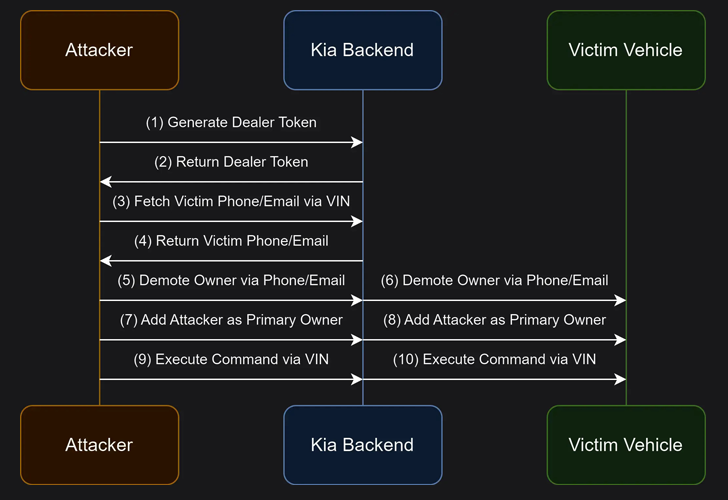
This attack makes use of flaws in Kia’s dealership system architecture (kiaconnect.kdealer[.]com), while attackers could create a Φictitious recognition online stead for themselves by means of an http request wherein access tokens were produced. Those tokens obtained previously were used on yet another http request to a dealer Apigw endpoint and the VIN number of the car to get the owner’s sensitive details.
The researchers also found that gaining access to a victim’s vehicle is as simple as four HTTP requests, allowing them to execute online driving commands:
- Create the dealer token and remove the “token” header from the HTTP response using the method described above.
- Get the victim’s email address and phone number.
- Change the owner’s existing login with the leaked email address and VIN number to make the attacker the primary account owner.
- Include the attacker’s email as the primary owner of the vehicle, to enable arbitrary commands to be executed.
“The vehicle was accessible and the victim had no information as to whether their license had been changed,” investigators said.
“An attacker could easily access their VIN through someone’s licensed API, then passively follow them or send dynamic commands to unlock, start and tornado the car.”
In a hypothetical attack, a threat actor could input a Kia vehicle’s license plate into a custom dashboard, retrieve the victim’s information, and execute commands on the car within approximately 30 seconds.
After responsible disclosure in June 2024, Kia patched the vulnerabilities by August 14, 2024. There is no indication that these flaws were ever exploited in real-world attacks.
“Vehicles will continue to have vulnerabilities, just as a code change at Meta could allow someone to take over your Facebook account. Similarly, car manufacturers could introduce changes that compromise your vehicle,” the researchers explained.
0 Comments
No comments yet. Be the first to comment!













Post a comment