The hacktivist group known as Twelve has been observed using publicly available tools to launch destructive cyber attacks against Russian targets.
“Instead of demanding a ransom to decrypt data, Twelve encrypts victims’ data and then destroys their infrastructure using a wiper, preventing any recovery,” Kaspersky stated in a Friday analysis. “This approach indicates a desire to inflict maximum damage on target organizations without seeking financial gain.”
Formed in April 2023 amid the Russo-Ukrainian war, Twelve has a history of launching attacks designed to cripple networks and disrupt business operations. The group has also engaged in hack-and-leak activities, exfiltrating sensitive information and sharing it on its Telegram channel.
Kaspersky noted that Twelve shares similarities in infrastructure and tactics with the ransomware group DARKSTAR (also known as COMET or Shadow), suggesting the two groups may be related or part of the same activity cluster. “While Twelve’s actions are clearly hacktivist, DARKSTAR adheres to the traditional double extortion model,” the cybersecurity firm added. “This variation in objectives highlights the complexity and diversity of modern cyber threats.”
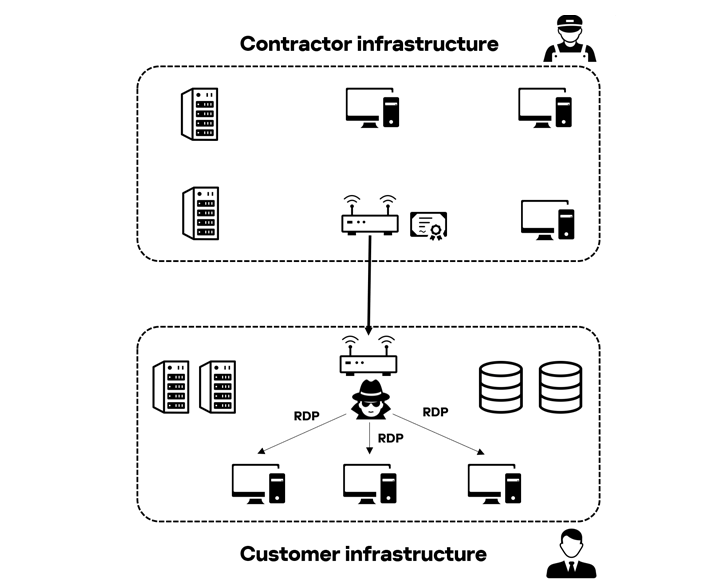
The attack process typically begins with abusing legitimate local or domain accounts to gain initial access, followed by the use of Remote Desktop Protocol (RDP) for lateral movement. Some attacks have been carried out via the victim’s contractors, using compromised contractor infrastructure to connect to the customer’s VPN and access their systems through RDP.
Twelve employs various tools such as Cobalt Strike, Mimikatz, Chisel, BloodHound, PowerView, adPEAS, CrackMapExec, Advanced IP Scanner, and PsExec for credential theft, discovery, network mapping, and privilege escalation. Malicious RDP connections are tunneled through ngrok.
The group also deploys PHP web shells like WSO, which are available on GitHub, to execute arbitrary commands, move files, or send emails.
In one incident investigated by Kaspersky, the attackers exploited known security vulnerabilities in VMware vCenter, such as CVE-2021-21972 and CVE-2021-22005, to deploy a web shell, which was then used to install a backdoor named FaceFish.
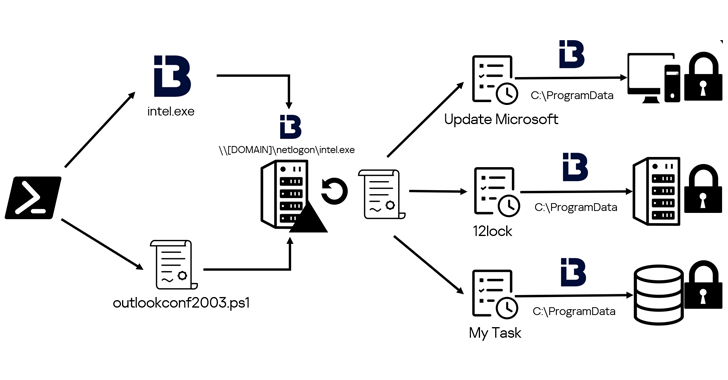
“To establish a foothold in the domain infrastructure, the adversary used PowerShell to add domain users and groups, and modify ACLs (Access Control Lists) for Active Directory objects,” Kaspersky reported. “To avoid detection, they disguised their malware and tasks under the names of existing products or services.”
The group used names like “Update Microsoft,” “Yandex,” “YandexUpdate,” and “intel.exe” to masquerade as legitimate programs from Intel, Microsoft, and Yandex, attempting to evade detection.
The attacks also involved using a PowerShell script named “Sophos_kill_local.ps1” to disable processes associated with Sophos security software on the compromised system.
In the final stages, the attackers utilized Windows Task Scheduler to execute ransomware and wiper payloads after gathering and exfiltrating sensitive information via DropMeFiles in the form of ZIP archives.
“The attackers deployed a version of LockBit 3.0 ransomware, compiled from publicly available source code, to encrypt data,” Kaspersky researchers explained. “Before beginning encryption, the ransomware terminates processes that could interfere with file encryption.”
The wiper, similar to the Shamoon malware, overwrites the master boot record (MBR) on connected drives and replaces all file contents with randomly generated bytes, making system recovery impossible.
“Kaspersky noted that the group relies on a familiar set of publicly available malware tools, suggesting that they do not create their own. This makes it possible to detect and prevent Twelve’s attacks in a timely manner,” the report concluded.
0 Comments
No comments yet. Be the first to comment!









Post a comment